Salesforce security: best practices for ensuring data protection and Salesforce security: concepts ~ hello salesforce! Salesforce developer beginner series: episode-10: salesforce security model
Salesforce Security Model – Explained » PantherSchools
Salesforce security model data sharing level explained record visually often referred comes where
Salesforce understand simplest
An overview of the salesforce security modelSalesforce data security model – james derflinger Salesforce security model – rangerinc. – digital transformation onSalesforce record access: who sees what and why.
Salesforce data security model explainedWhat is salesforce security model? salesforce security model tutorial guide Salesforce zielsetzung bloofusion settings anzeigengestaltungSalesforce data security model. salesforce is the world’s #1 customer.

Salesforce data records hierarchy visibility visually triangle trailhead registros acesso acceso permissions defaults mirketa src
Salesforce hierarchy seesA guide on salesforce security models Exploring on salesforce: salesforce lightning platform security and sharingSimplest flow diagram possible to understand different access in.
Salesforce security modelSalesforce security model Introduction to the salesforce security modelAccess salesforce security certified demand edit read.
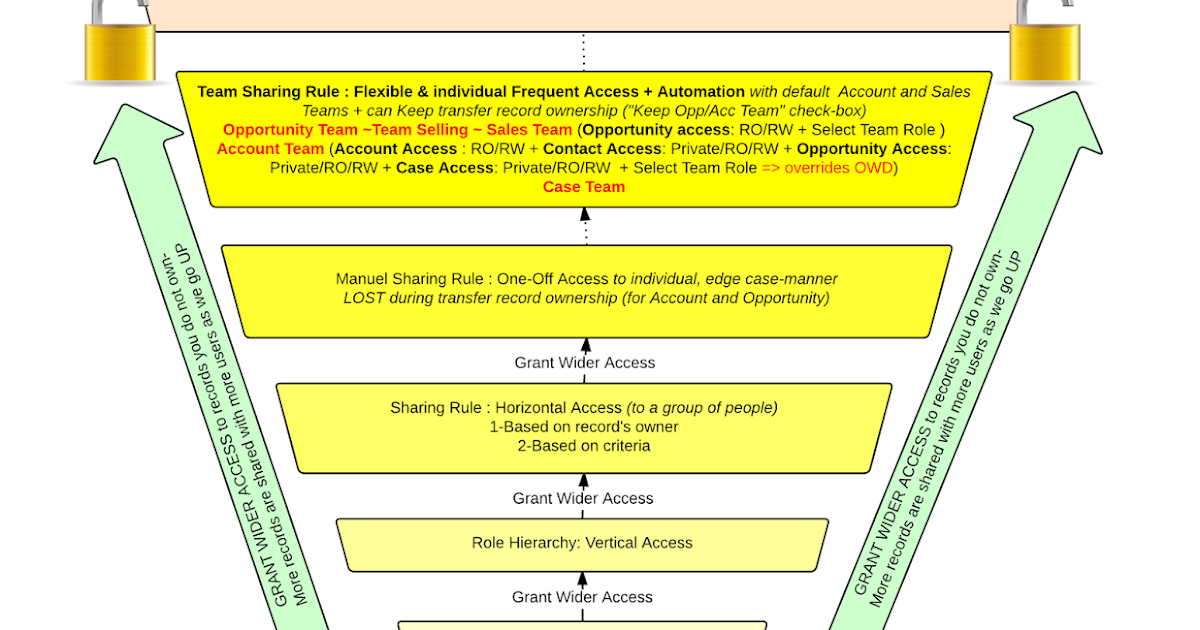
What is data security in salesforce ?
Salesforce explained object inspireSalesforce data security model Salesforce data security model — explained visuallySalesforce data security model — explained visually.
The data access security modelSalesforce security model — an overview Salesforce security model data access levels organization entire usersSalesforce security model explained forcetalks.

Salesforce security model: its four key components
Salesforce securityThe three pillars of salesforce security Salesforce sharing model and data securitySalesforce crm.
What is the salesforce data security modelSalesforce data security model explained visually salesforce Chatbot integration with salesforce helps to generate better roiSalesforce integration chatbot bot diagram business delivering commands.

Salesforce security controls detect transactions erroneous suspicious analytics advanced access
Introduction to the salesforce security modelSalesforce security: concepts ~ hello salesforce Security platform lightning salesforce architecture cloud sharing further reference salesSalesforce security model – explained » pantherschools.
Security salesforce sharing permission level sets system roles profiles concepts model explanation good userSalesforce data security model Salesforce developer beginner series: episode-10: salesforce security modelChoose the right salesforce security settings unit.







